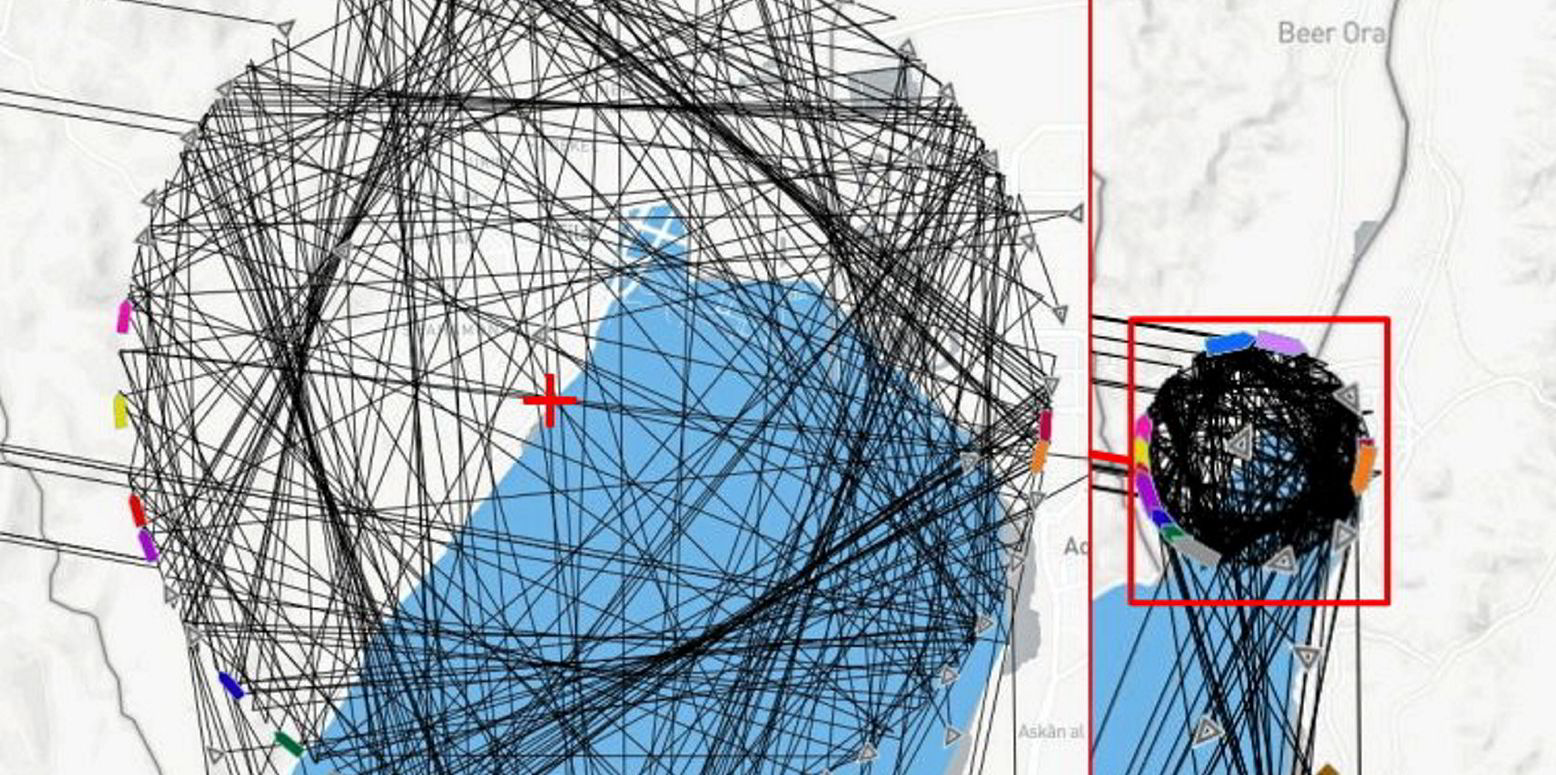
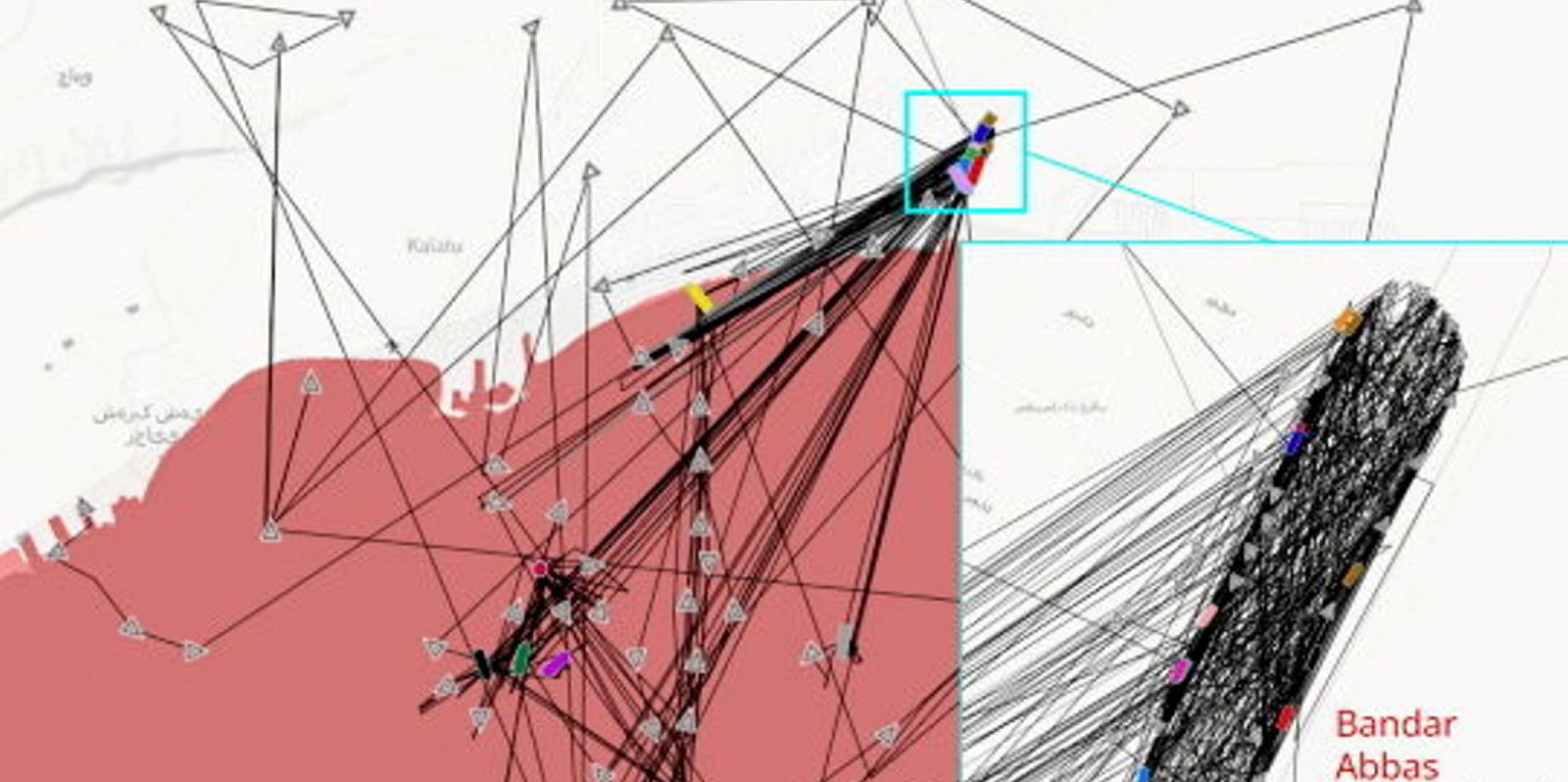
Israel is likely to have manipulated vessel satellite data to help protect itself from the Iranian missile attack launched on 13 April, UK analysis company Geollect believes.
A graphic of “spoofed” AIS positions provided by the company shows a ball of positions over the Israeli city of Eilat in the Gulf of Aqaba.
Geollect told TradeWinds: “This is global navigation satellite system (GNSS) manipulation which has affected the AIS data being broadcast.
“The exact root cause of this is still to be determined,” the company added.
The pattern was recorded from 23:34 UTC on 13 April for almost 24 hours.
Geollect described this as “a series of almost certainly manipulated AIS positions”.
This coincided precisely with the timing of the Iranian missile and drone strikes against Israel.
The centre point was located over Eilat Naval Base.
“It is highly likely that the mass AIS manipulation identified over Eilat was conducted as a defensive measure by Israeli forces to protect the Eilat Naval Base from precision-guided drones and missiles by disrupting the GNSS signals,” Geollect said.
The company explained that the short time frame strengthens the assessment that the manipulation was conducted as a measure to protect a key site which had already been struck once before in the same month.
The Eilat Naval Base is home to the Israeli Navy’s 915 Squadron, which is focused on maritime security in the Red Sea.
“Due to the significant increase in hostilities since the 7 October attack and the Houthis’ actively targeting Israeli affiliated shipping in the Red Sea, it has almost certainly increased the importance of the naval base as a means of facilitating and enabling high-tempo maritime operations,” Geollect said.
Eilat is Israel’s only Red Sea port.
Last year, AIS data was manipulated to show vessels doing more than 50 knots over land in Iran.
Geollect identified several incidences of what it said was almost certainly deliberate large-scale spoofing of vessels’ AIS there.
This had occurred over three months, involving complex patterns and up to 60 ships.
Also in 2023, Geollect noted mass spoofing that produced a giant Russian pro-war Z symbol in the Black Sea.
The manipulation created a Z measuring 65 km in length, visible on open-source tracking software.